Assuming an application is for internal use only (containing sensitive information), there are 3 ways to implement an authentication system.
- Self-implementation.
- Using third party auth providers like Google or Auth0.
- Using Identity-aware Proxy.
Between the 3 choices, self-implementation is too much of a hassle, so only (2) and (3) are most likely the way to go.
Using third party providers is the most well-known choice (e.g., Auth0), and it also offers ability to setup authorization mechanism (e.g., I can see my folder, but am I allowed to see admin panel?)
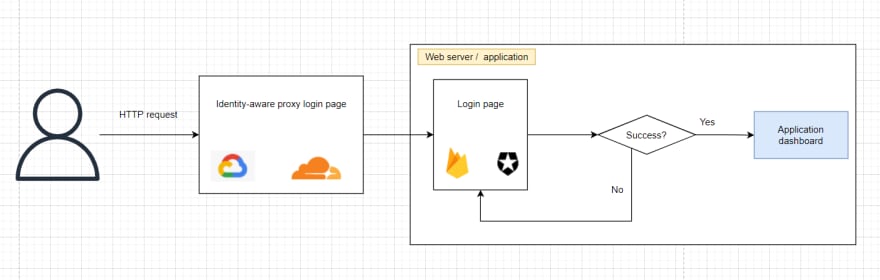
Identity-aware Proxy on the other hands is an authentication layer to prevent your request from reaching the server. It is used to replace VPN in cloud environment. In a sense, it also offers simple authorization as you can declare which group of users can reach the web server (not down to endpoint level though).
You can have both authentication mechanism implemented in your application, and an Identity-aware Proxy enabled.
With that said, for an internal web application (with sensitive information), is using only Identity-aware Proxy enough if there is no complex authorization involved? What are the downsides?
If you are using both at the same time, why? Also, if both Identity-aware Proxy and application login page use the same authentication provider (e.g., Google SSO), does it make the login page become redundant?